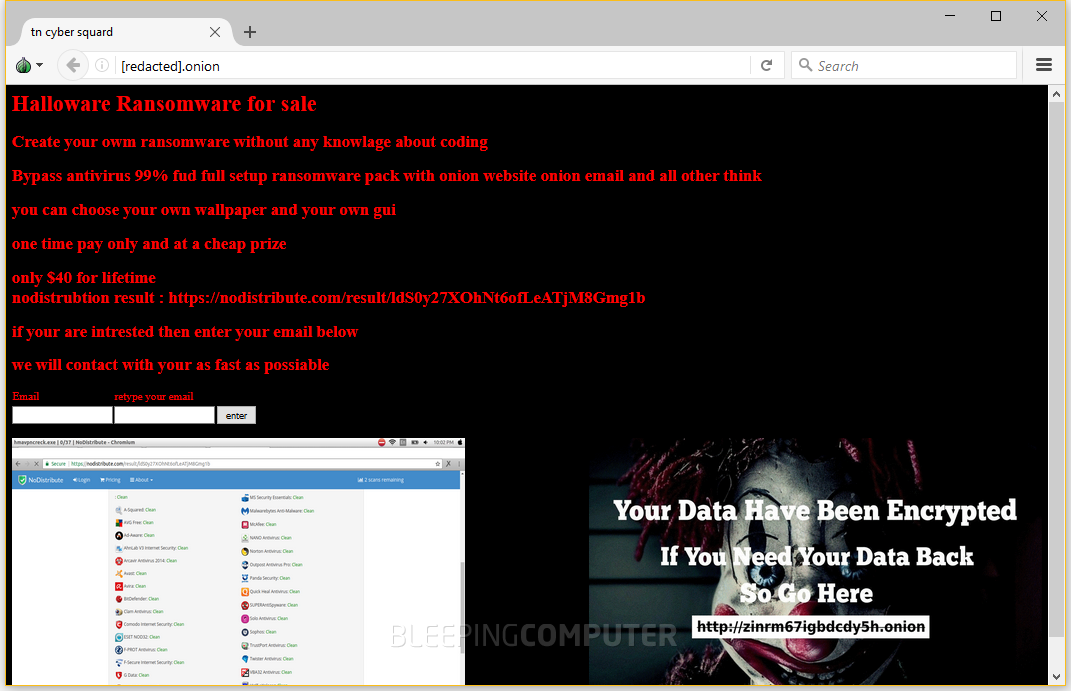
A malware author by the name of Luc1F3R is peddling a new ransomware
strain called Halloware for the lowly price of $40. Based on evidence
gathered by Bleeping Computer, Luc1F3R started selling his ransomware
this week, beginning Thursday.
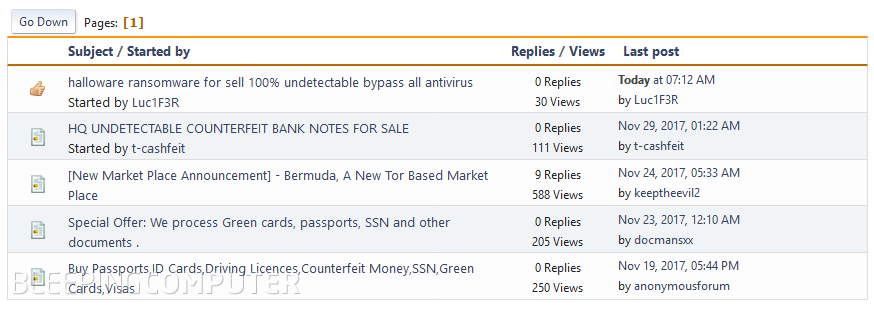
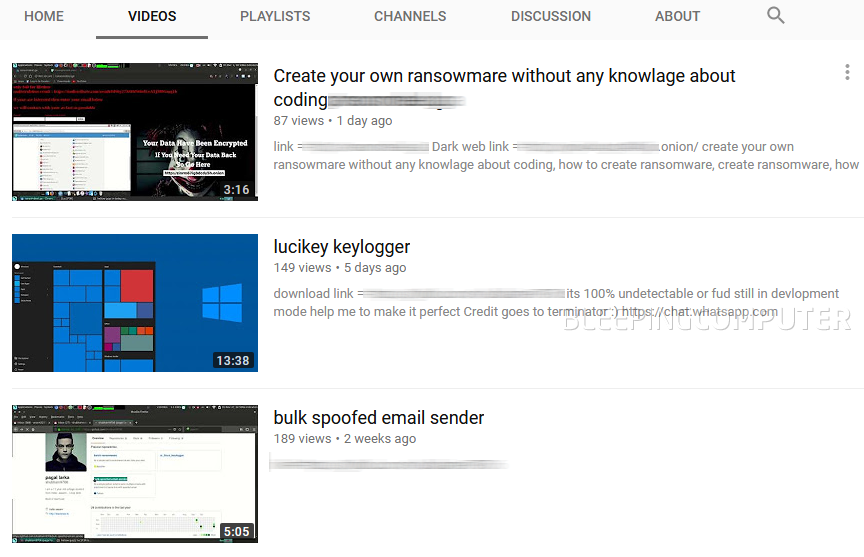
Currently, the malware dev is selling and/or advertising his ransomware on a dedicated Dark Web portal, on Dark Web forums, two sites hosted on the public Internet, and via videos hosted on YouTube.
The sites are offering a lifetime license for the Halloware ransomware for only $40. This lowly price tells us three things. The offer is either too good to be true, Halloware is a scam, or the ransomware is not as sophisticated as Luc1F3R believes.
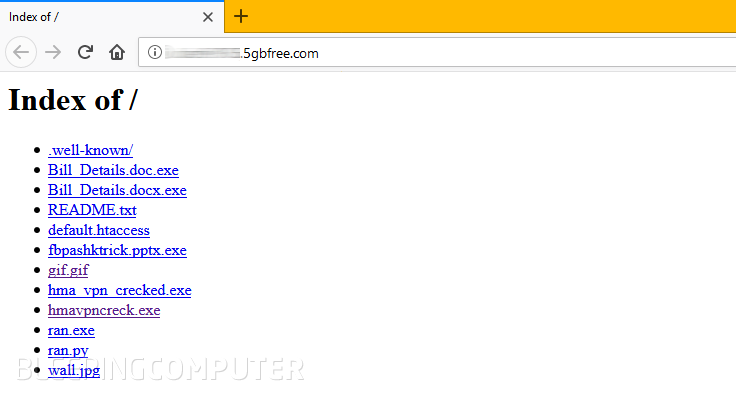 The file hmavpncreck.exe had the same SHA256 hash for which Luc1F3R included NoDistribute scan results in Halloware's ad, confirming we found the correct file.
The file hmavpncreck.exe had the same SHA256 hash for which Luc1F3R included NoDistribute scan results in Halloware's ad, confirming we found the correct file.
Furthermore, the site also hosted a file named ran.py, which looked to be Halloware's source code. While the file was protected, Bleeping Computer managed to extract its source code, which will end up in the hands of other security researchers to create decrypters, in case someone buys this ransomware and uses it to infect real users.
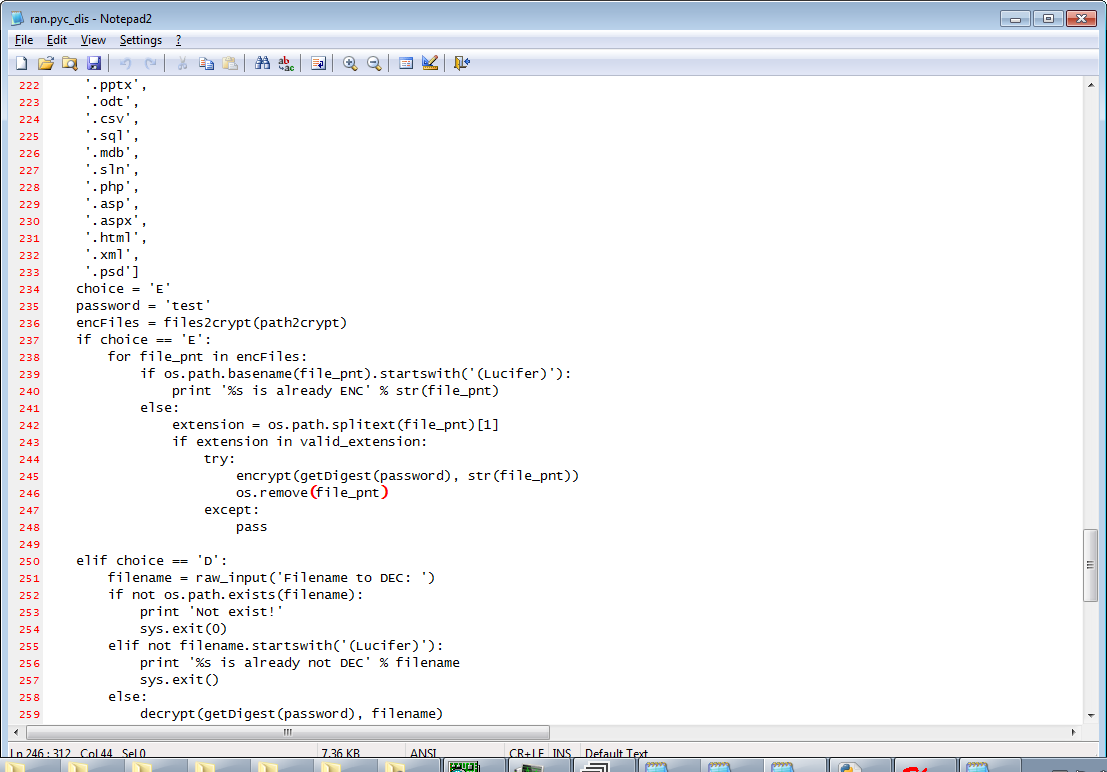
While Halloware was a simplistic ransomware, it did work. Several of the weaponized files hosted on Luc1F3R's website encrypted files on our test machines.
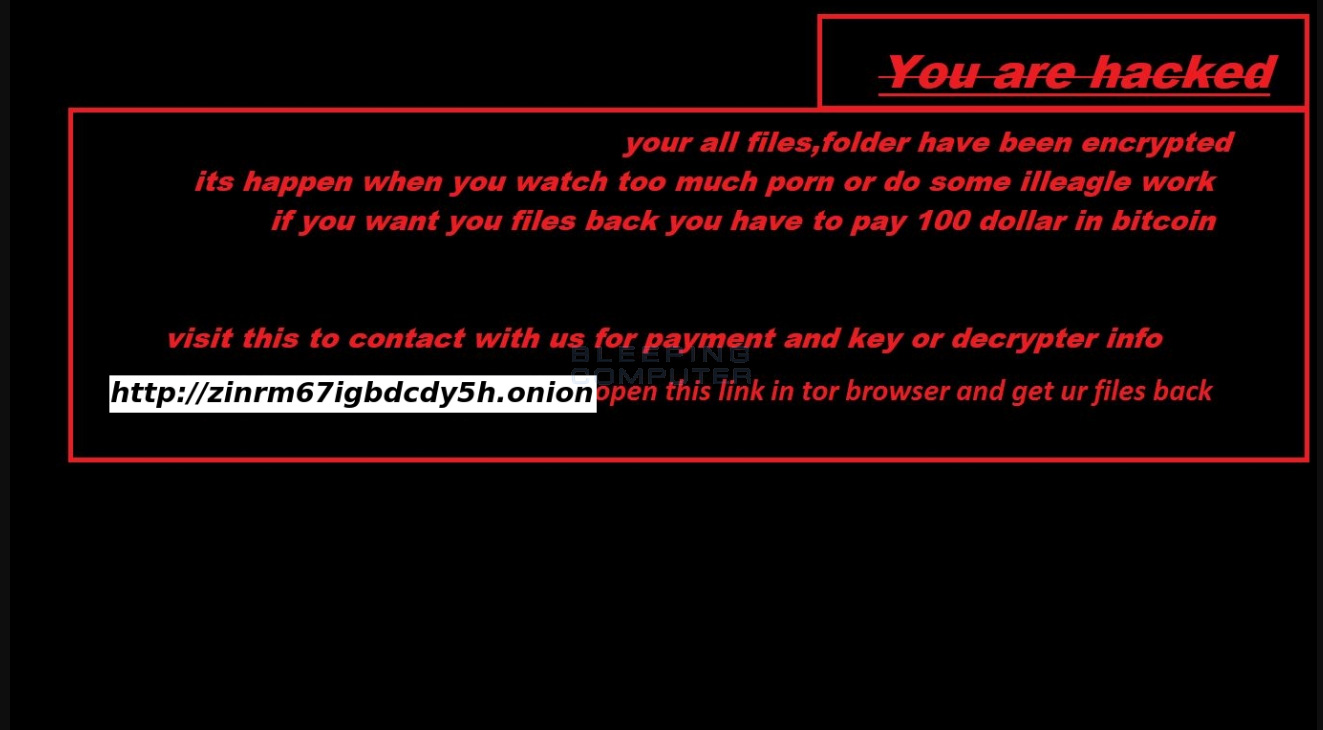
The ransomware encrypts files using a hardcoded AES-256 key and prepends the "(Lucifer)" string to encrypted files. For example, once encrypted, image.png will become (Lucifer)image.png.
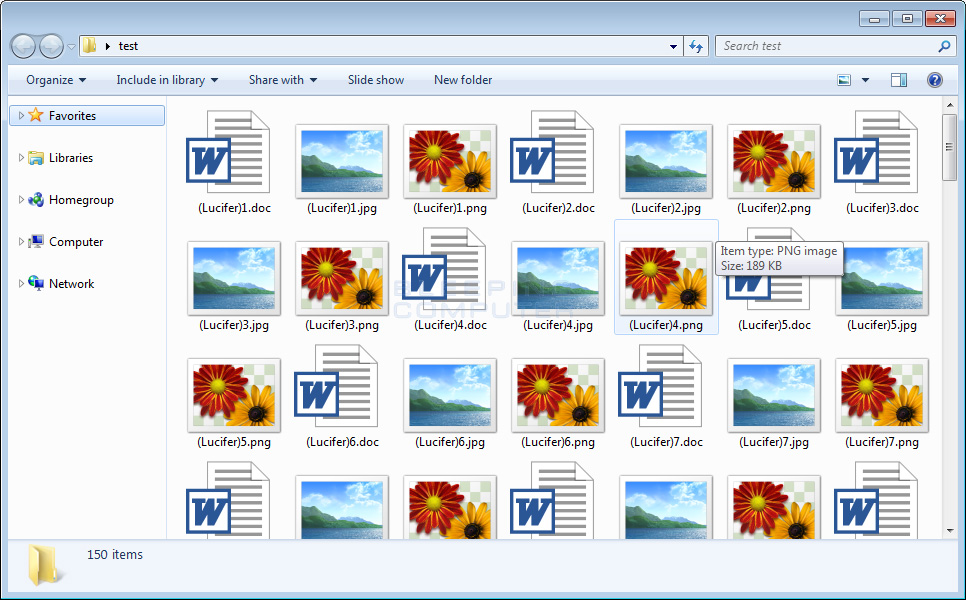
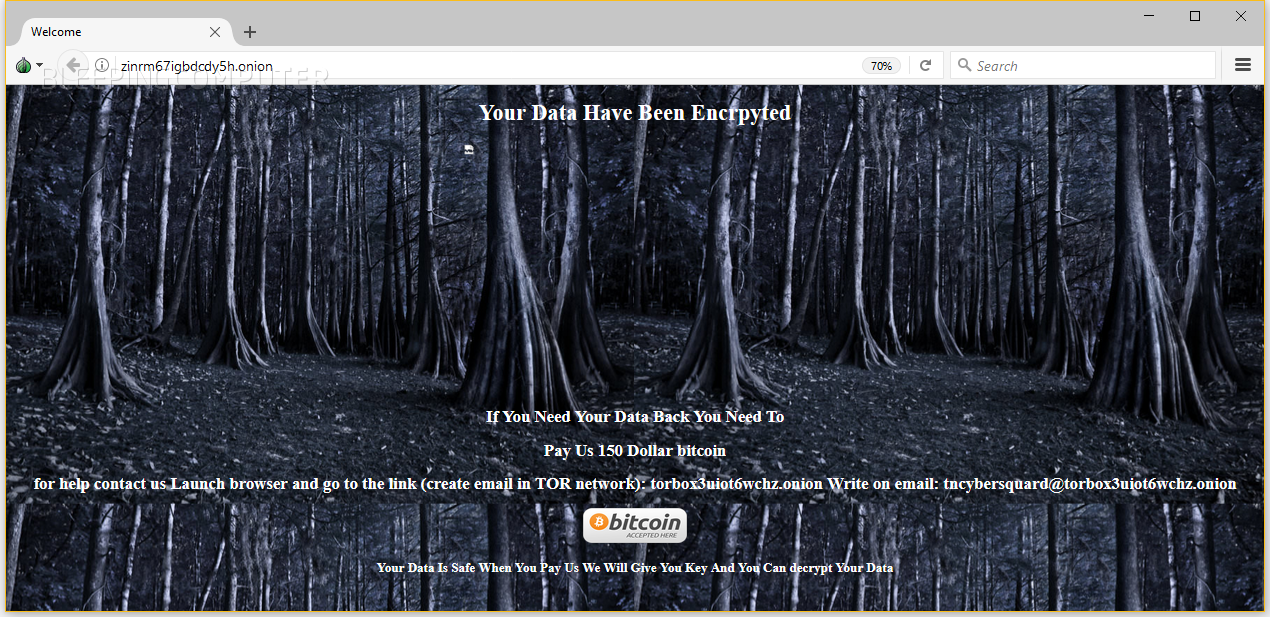
Once the encryption process ends, the Halloware ransomware pops up a window showing a creepy clown with a ransom message directing victims to a Dark Web payment portal, and changes the user's desktop wallpaper with a similar message. Halloware does not drop text files with ransom notes on the infected PCs.
All a buyer needs to do is to change two images and add his own with a customized payment site URL.
Despite this, because the ransomware uses a hardcoded AES key and does not save any information on a remote server, Luc1F3R has no chance of making any money off Halloware. The crook should just close shop because no sane or experienced malware distributor will ever bother spending $1 on this strain, let alone $40.
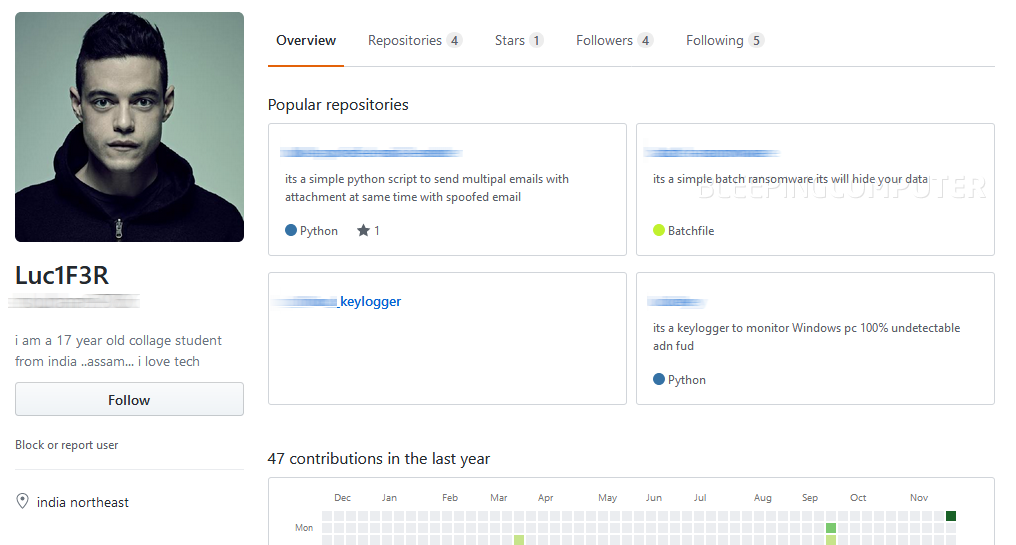
Some of these videos also link to his GitHub account, where Luc1F3R is hosting four other malware strains: a Batch-based ransomware, a Windows keylogger, a Linux keylogger, and a bulk spoofed email sender.
Luc1F3R also claims to be a 17-year-old college student from Northeast India. Since Luc1F3R used such poor OpSec, don't be surprised if that's his real location.
Currently, the malware dev is selling and/or advertising his ransomware on a dedicated Dark Web portal, on Dark Web forums, two sites hosted on the public Internet, and via videos hosted on YouTube.
 |
 |
 |
The sites are offering a lifetime license for the Halloware ransomware for only $40. This lowly price tells us three things. The offer is either too good to be true, Halloware is a scam, or the ransomware is not as sophisticated as Luc1F3R believes.
Tracking down Luc1F3R's sites
While Bleeping Computer initially thought this was a scam, thanks to several operational mistakes in the websites selling the ransomware, we managed to track down a web page where Luc1F3R was hosting Halloware-related files, including weaponized documents for infecting victims with the ransomware.
Furthermore, the site also hosted a file named ran.py, which looked to be Halloware's source code. While the file was protected, Bleeping Computer managed to extract its source code, which will end up in the hands of other security researchers to create decrypters, in case someone buys this ransomware and uses it to infect real users.

While Halloware was a simplistic ransomware, it did work. Several of the weaponized files hosted on Luc1F3R's website encrypted files on our test machines.
The ransomware encrypts files using a hardcoded AES-256 key and prepends the "(Lucifer)" string to encrypted files. For example, once encrypted, image.png will become (Lucifer)image.png.

Once the encryption process ends, the Halloware ransomware pops up a window showing a creepy clown with a ransom message directing victims to a Dark Web payment portal, and changes the user's desktop wallpaper with a similar message. Halloware does not drop text files with ransom notes on the infected PCs.



All a buyer needs to do is to change two images and add his own with a customized payment site URL.
Despite this, because the ransomware uses a hardcoded AES key and does not save any information on a remote server, Luc1F3R has no chance of making any money off Halloware. The crook should just close shop because no sane or experienced malware distributor will ever bother spending $1 on this strain, let alone $40.
Tracking down Luc1F3R
Luc1F3R is a low-skilled actor and appears to be taking his first steps in the world of cyber-crime. All the hacking tutorials he uploaded on YouTube describe basic techniques or promote unsophisticated malware.Some of these videos also link to his GitHub account, where Luc1F3R is hosting four other malware strains: a Batch-based ransomware, a Windows keylogger, a Linux keylogger, and a bulk spoofed email sender.
Luc1F3R also claims to be a 17-year-old college student from Northeast India. Since Luc1F3R used such poor OpSec, don't be surprised if that's his real location.

IOCs:
Hashes:
007c1f11afb195d77c176891d54b9cfd37c87b13dfe0ab5b6c368125e4459b8c d5b58bdda4ece79fbc264fff7f32df584d7b0051a5493119d336252f4668c73c c6d2e486109dc37f451dccce716e99e8a2653475d5605531d52756fc4fc88f09Files targeted for encryption:
.jpg, .jpeg, .raw, .tif, .gif, .png, .bmp, .3dm, .max, .accdb, .db, .dbf, .mdb, .pdb, .sql, .dwg, .dxf, .c, .cpp, .cs, .h, .php, .asp, .rb, .java, .jar, .class, .py, .js, .aaf, .aep, .aepx, .plb, .prel, .prproj, .aet, .ppj, .psd, .indd, .indl, .indt, .indb, .inx, .idml, .pmd, .xqx, .xqx, .ai, .eps, .ps, .svg, .swf, .fla, .as3, .as, .txt, .doc, .dot, .docx, .docm, .dotx, .dotm, .docb, .rtf, .wpd, .wps, .msg, .pdf, .xls, .xlt, .xlm, .xlsx, .xlsm, .xltx, .xltm, .xlsb, .xla, .xlam, .xll, .xlw, .ppt, .pot, .pps, .pptx, .pptm, .potx, .potm, .ppam, .ppsx, .ppsm, .sldx, .sldm, .wav, .mp3, .aif, .iff, .m3u, .m4u, .mid, .mpa.wma, .ra, .avi, .mov, .mp4, .3gp, .mpeg, .3g2, .asf, .asx, .flv, .mpg, .wmv, .vob, .m3u8, .mkv, .dat, .csv, .efx, .sdf, .vcf, .xml, .ses, .rar, .zip, .7zip, .jpg, .jpeg, .txt, .doc, .docx, .xls, .xlsx, .ppt, .pptx, .odt, .csv, .sql, .mdb, .sln, .php, .asp, .aspx, .html, .xml, .psd

No comments:
Post a Comment